Password management
Choosing good passwords
The best way to choose your password is to not choose it. To do so you generate your password randomly using the diceware method or using a password generator.
I won’t go into details about why your current password is not strong enough. If you use the same password everywhere, there is a good chance that one of the services you have subscribed to leaked your password, which unlocks all others sevices.
If you use your “own” password algorithm, well, the same argument applies. One of your password has been leaked, and if I see that it’s “!1Dropbox”, I can guess that your Gmail password will be “!1Gmail”.
About password entropy
Here is a simple definition given by TechTarget:
Password entropy predicts how difficult a given password would be to crack through guessing, brute force cracking, dictionary attacks or other common methods.
We usually measure a password entropy in bits. If your password is known, it has an entropy of 0. If half the time I need 6 tries to find it, it has 6 bits of entropy.
The formula to calculate entropy is simple. If you have a password with:
- a pool of 26 possible characters (lowercase a-z)
- 8 characters in your password
Then the entropy is 8*log2(26) which is about 37.6 bits of entropy.
That formula only works if your password has been chosen randomly. And entropy qualifies the process of choosing the password. Not the password itself.
But how much entropy should your password have ? Well that depends on the attacker’s computing power.
Let’s say your attacker can try 100 billion passwords per seconds. And your password entropy is 40. Then it will take 11 seconds for the attacker to brute-force your password. For the record, NSA can do 10 trillion guesses per second, and someone with around 2000$ can do 100 billion guesses per second.
Here is a very good chart made by /u/HelmedHorror that sums up the time required to crack a password according to its entropy.
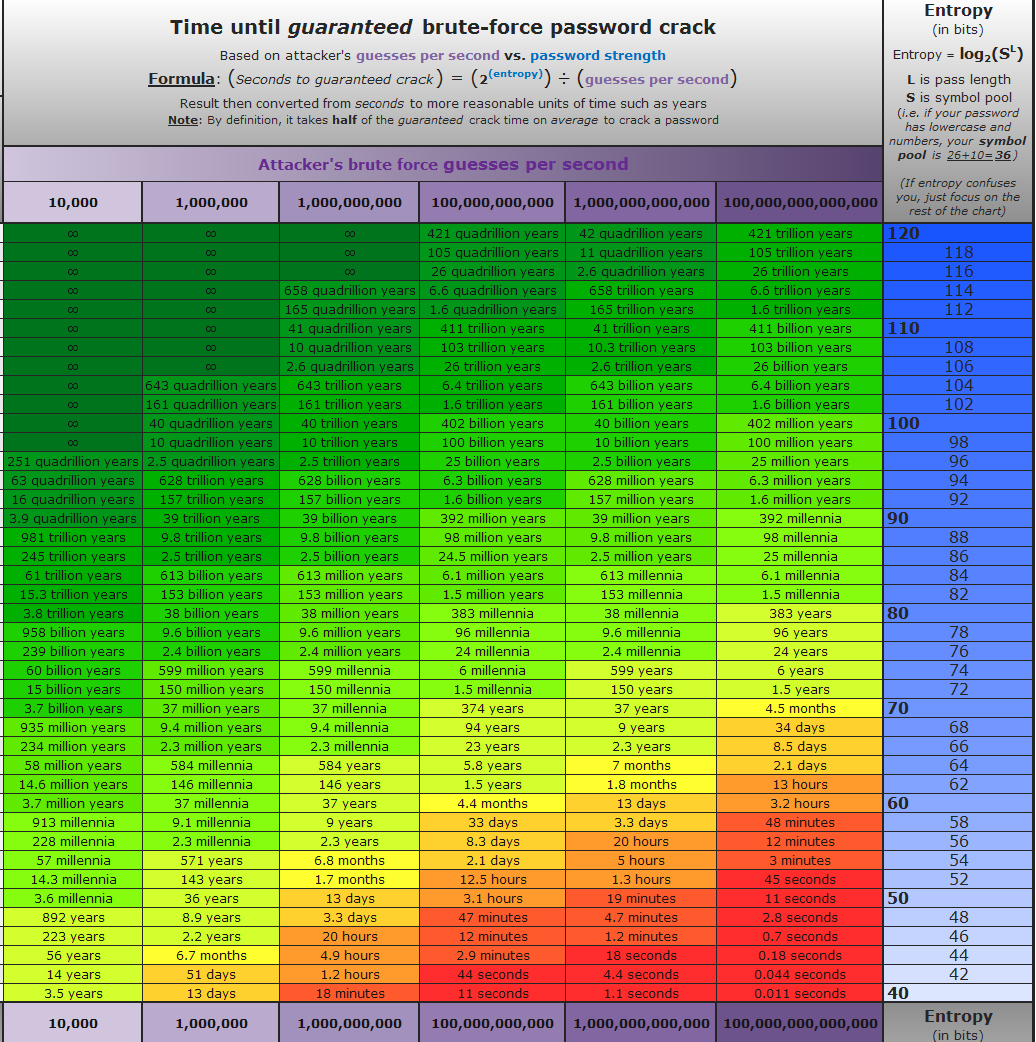
In conclusion, a password entropy of at least 80 is pretty good.
Generate a password with the Diceware method
Password entropy only works if your password was chosen truly randomly. But how can you choose a password that :
- is long enough to have enough entropy
- is easy to remember ?
You can use the Diceware method! The method is simple, you roll a dice multiple times and write down the numbers you got. Then you map these numbers to words from a word list. The result is a password that looks like this:
current-gizzard-spellbind-hummus-curtain
To help you remember this password, you can use the peg system, a memory trick used by magicians and mentalists.
Since each word is chosen between a list of 7776 words, and the password contains 5 words, the entropy is 77!
Generating a word
To generate a word in your password:
- First download the word list generated by the EFF.
- Roll a dice 5 times and note the numbers you got :
44643 - Check the list to find the word associated to
44643: porous
Repeat this steps for each word.
If you get a list of words that makes a sentence. Generate a new password.
As a final note, you will need to change passwords for each site. That way, when your password for Dropbox is found, your Gmail account is still secure. But how can you remember all those passwords? Use a password manager.
And if you are up to the challenge, you can the use peg system to remember all of your passwords !
Keepass
Keepass is an open source password manager that stores your passwords securely. You install it on your computer, your phone, your tablet and import your Keepass database on all these devices.
The database is encrypted, which means you need a password to decrypt it. This password will be the only one you will need to remember.
Your Keepass password is the key to all of you other passwords, so be sure to generate a password with a very high entropy for Keepass (use 8 or even 12 words!).
Keepass also integrates a password generator. Which is great when some websites have stupid rules like :
- have at least 1 number
- have at least 1 special character
- etc …
If you ever fall in this situation, you can use Keepass to generate a random password that match the site’s rules.
Changing passwords
It is already a good security practice to have a different password for each site, each password having a high entropy. But even with a high entropy, it isn’t far-fetched to think that a government that has decided to target you specifically could break your password in less than a year. That is why you should change your passwords regularly (even your Keepass password).
Going further
Now that you have good passwords, you should look into two factor authentication (2FA). The idea is simple : you possess a physical token (a usb key, a phone) that is unique. Now when you want to login to a website with 2FA, you have to:
- Enter your username.
- Enter your password (you’re supposed to be the only one knowing it).
- Activate your physical token (you’re supposed to be the only one having it).
That way if your password is compromised, the attacker won’t be able to access the website as long as he doesn’t have access to your physical token.
